This is the latest tutorial in our series focusing on encrypting your email. In the first tutorial, we introduced the general concepts of encryption and how they can be used to secure and authenticate our emails. In the second tutorial, I guided you through installing encryption software on your computer and getting started sending your first messages. In the third episode, I introduced you to Keybase, a service designed to strengthen the Web of Trust. And, in the fourth tutorial, I reviewed Mailvelope, a browser extension for sending and receiving encrypted emails. In addition to reading the earlier episodes, you may want to check out the Electronic Frontier Foundation's Surveillance Self-Defense Guide.
In this tutorial, I'll introduce you to iPGMail, an iOS application that makes the sending and receiving of encrypted messages more manageable on smartphones and tablets. I'll also cover some of the vulnerabilities inherent in carrying your private key on your device.
In upcoming episodes, as part of the series on managing your digital assets after your death, we'll use what we've learned to create a secure cache of important information for your descendants in case of emergency.
Just a reminder, I regularly participate in the discussions below. If you have a question or topic suggestion, please post a comment below. You can also follow me on Twitter @reifman or email me directly.
What's iPGMail?
Now that we've begun using encrypted messaging on the desktop and in the browser, it makes sense to ask if we can use it from our devices. The answer is yes, but not without some usability limitations and minor security risks.
iPGMail is an iOS application that helps you send and receive encrypted messages on an iPhone or iPad. iPGMail costs $1.99 at the App Store. It's written by developer Wyllys Ingersoll.
The application makes it possible to store your private key and others' public keys on your device and to send and receive encrypted messages on the go.
Getting Started With iPGMail
If you want to follow along, you'll need to purchase iPGMail at the App Store for $1.99 (it's worth it):

Once you're running iPGMail on your phone, it's time to generate or import our public and private key.
Import Your Key Pair
Initially in iPGMail, you'll see an empty public key listing. Click Private to go to the private key listing:

If you've followed along with our earlier tutorials, you're already using a key pair. If you need to generate a new key pair, iPGMail can do that for you. Just click the + sign in the upper right:

Importing an Existing Private Key
Here's where things get tricky. A private key string is quite long, not easily typed into a phone. It's also likely living on your desktop machine or a USB key—not easily transferred to a phone.
I know what you're thinking, but emailing your private key to yourself would expose it to a number of possible security threats. Placing it in Dropbox would expose it to probable government surveillance.
One way is to use iTunes File Sharing to transfer your private key .asc file to your phone. I prefer to use AirDrop. Personally, I find the AirDrop interface between iOS and Mac OS X to be fairly counterintuitive and only intermittently reliable—yet it is still far more successful than trying anything these days with the pathetic usability black hole which is iTunes. However, if AirDrop works well, this is a great use case for it.
Caution: Only use AirDrop for this on a secure WiFi network.
Enable AirDrop on your device. Then, on OS X, right click on your private key .asc file, select Share > AirDrop, and click your profile name. You'll see something like this:
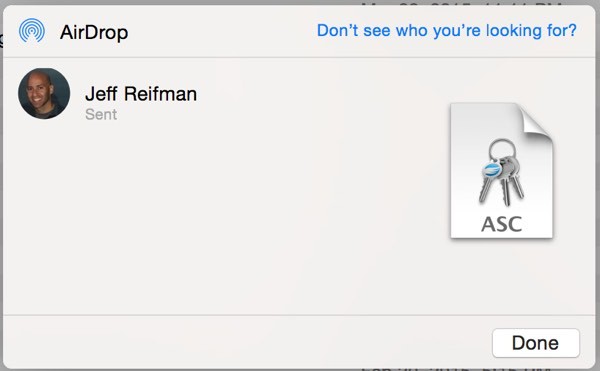
When you click on the file on your device, AirDrop will allow you to open it in iPGMail:

There's my private key listed in iPGMail—you can find me at Keybase:

The Safety of Your Private Key
The root of PGP security relies on you keeping your private key completely private and safe. Carrying it around on a device connected to the Internet makes it inherently vulnerable.
In iPGMail's FAQ, they describe a variety of layers they use for protecting your key:
- The entire database used to hold all of the PGP keys is stored in an encrypted format on disk and cannot be read from or written to while the device is locked or booting.
- The private keys in the DB (which is itself already encrypted) are also protected with a key derived from your private key passphrase, so choose a strong passphrase for your secret keys.
- You can set the app Pin Protection in the settings for the app to force you to enter a unique 4-digit passcode to unlock the app. On newer iPhone and iPad models, this also enables you to use the Touch ID feature.
- Make sure you have enabled the stronger passcode lock in the iOS settings.
To choose a robust passphrase for your key, I suggest reading The Intercept's recent column on dice-generated passwords.
The more robust your passphrase, the more difficult it can be to regularly type it in on a device such as an iPhone. This is one of the inherent usability issues with iPGMail and encryption on your iPhone.
Sending an Encrypted Message
Before you can begin sending an encrypted message, you need to import the public keys of recipients that you may want to correspond with. iPGMail has made this fairly straightforward.
Import Public Keys
iPGMail offers public key search and lookup from PGP.net and Keybase; we explored the latter in It's Time To Encrypt Your Email: Using Keybase (Tuts+).
Click the + sign in the upper right and select Search Keybase. I'm going to send a note to Keybase founder Chris Coyne.

iPGMail lets me search for "chriscoyne":

Click the Key Fingerprint and import the key. You can see my eventual public keys listed below:

Compose Your Message
To send a message, click the Compose icon at the bottom of the screen. Click the + sign on the To: line to select one of your public key recipients. Then, type a Subject and write your message:

Here's what it looks like to select your recipient's public key:

iPGMail will use this public key to encrypt the message for the recipient.
Send Message Directly or Copy to Clipboard
iPGMail can send your message using your device's SMTP settings, or it can fill your clipboard with the encrypted message to paste into your own mail program, i.e. Send Email or Copy to Clipboard:

Now let's take a look at decrypting inbound messages.
Receiving an Encrypted Message
Messages With Encrypted Attachments
Here's the message I received back from Chris Coyne, encrypted inside attachments:

When I click on encrypted.asc, my iPhone allows me to Open in iPGMail:

Here's one of the places where iPGMail will ask for your passphrase. It's definitely a usability burden in place to preserve security:

Chris didn't sign his message (perhaps it was sent by an impostor), hence the red X, but you can see the decrypted attachments below and click on them to read the message:

Messages With Encryption in the Message Body
Here's an encrypted message I received where the secret is plaintext in the message body. I use my iPhone to copy the entire PGP Message:

iPGMail nicely uses clipboard detection and immediately when I switch over to the app, it asks if I want to Import the message:

Then, it displays the secret message for me. I've blacked it out because, well, it's secret (don't worry, my life's really not that exciting):

Working With Secure Files
On the iPGMail Settings page, you can integrate your iCloud and Dropbox clouds:

This enables you to work with encrypted documents from the iPGMail Files page:

Closing Thoughts
iPGMail does a very nice job enabling basic encryption on iOS. I think it handles a number of difficult requirements of using PGP encryption relatively gracefully.
Yet it's unable at this time or does not simplify the usability of private key management on the iPhone to make it readily usable with all your messaging. It is certainly functional and capable for occasional encrypted messaging needs—and it's worth more than its $1.99 price tag.
Until Apple integrates secure messaging into Mail directly (or other solutions appear), this is the best PGP device messaging I can imagine. Regardless, I hope you're well on your way to encrypting more of your communications—from the desktop to the laptop and from the browser to your iPhone.
Please feel free to post your questions and comments below. You can also follow me on Twitter @reifman or email me directly. Browse my Tuts+ instructor page if you'd like to see other tutorials I've written.


Comments